Microsoft Azure Active Directory (now Microsoft Entra ID), commonly known as Azure AD, is a system in Microsoft Azure that enables identity management to configure user and group access to services and resources. With deviceTRUST Contextual Security, administrators now have a powerful new way to enforce all security, compliance and regulatory requirements securely and intelligently for Azure AD connected devices when accessing on-premises or cloud resources.
With the ever-increasing dynamic and mobile use of digital workspaces and their local and cloud resources, you need an IT security solution that does more than control access based on the user’s group membership in accordance with the specifications. Instead, it is necessary today to fully consider the context of access in addition to the user and their group memberships.
Microsoft Azure AD offers the solution of choice for this with conditional access control. With the help of conditional access, access to company resources can be controlled, for example, depending on the user and their group memberships as well as based on the context of the access. The context is generated from a few properties of the device used and is only available as a compliant status if the device is managed via Microsoft Intune.
Microsoft Azure AD device view with a Microsoft Intune managed device and its compliant status.
For most of our customers and prospects, however, this is not enough to meet their security, compliance and regulatory requirements. But why?
- Not all devices are managed with Microsoft Intune or Microsoft Intune will never be used to define the required compliant status.
- The information available to define the context is not sufficient. Much more information of the device, operating system, security components, network, location, etc. is needed for context definition.
- Not all applications and resources can be managed by a single compliant state in conditional access. Different applications have different compliance requirements that need to be considered.
- In addition to the corporate resources made available by Microsoft Azure AD, existing applications, such as an on-premises Citrix environment, should also be securely controlled by a compliance check during access.
- Definition and use of an enterprise-wide compliance requirement for access regardless of the deployment (cloud, on-premises and local) of the resource.
The deviceTRUST Contextual Security solution allows to fully address the above listed items!
For this reason, with the latest deviceTRUST version 21.1 (Release Notes), we have created the possibility to dynamically set the compliant status as well as other context information of a connected device in Azure AD. Regardless of how the devices are managed, with or without Microsoft Intune.
All context information that deviceTRUST can determine about the local or remote device is available to the IT administrator for this purpose. In addition, there are various actions that can be started when the context enters a certain state.
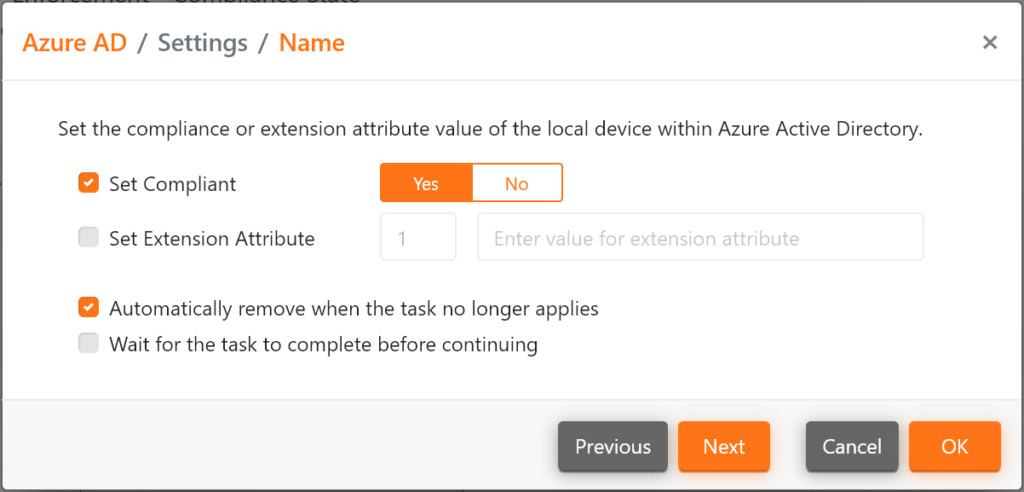
Definition of the compliant status depending on the status of the security components and communication of the status to Azure AD using the Azure AD task.
With the Azure AD task, not only can the compliant status be set depending on the statuses of the used contexts, but also the maximum of 15 extension attributes can be used for additional context information. For the evaluation of the individual task sequences, multiple contexts and their statuses can also be included in the decision.
Azure AD task to set the Compliant status.
Azure AD task to set the extension attribute 7.
Microsoft Azure AD device view with a device not managed by Microsoft Intune and its compliant status set by deviceTRUST.
Example 1: Compliant Status
Within the Azure AD Conditional Access policy, the compliant status set by deviceTRUST can then be used very easily.
Example 2: Extension attribute
Within the Azure AD Conditional Access policy, the extension attribute set by deviceTRUST can then be used very easily.
Conditional Application Access
In addition to controlled access to cloud-based applications via Azure AD and Conditional Access, applications are still installed locally. To enable access that meets the requirements here as well, deviceTRUST Contextual Security offers the possibility to control these with the Conditional Application Access function. For this purpose, deviceTRUST uses Microsoft AppLocker and handles the complete automated AppLocker configuration of the Allow List and the context-based application approval for local applications.
You can read more about Microsoft AppLocker integration in the following blog posts:
- Microsoft AppLocker Management with deviceTRUST (Link)
- Create and manage application Allow List with deviceTRUST (Link)
- Conditional Application Access with deviceTRUST (Link)
Summary
With deviceTRUST Contextual Security, the compliant status of the device within Microsoft Azure AD can now be set based on the very diverse context information about the local and/or remote device. For this purpose, a few valuable or wide-ranging context information can be processed. Likewise, there is the possibility to use other context information independently in addition to the compliant state. The use of those enterprise-wide contexts within the Azure AD environment, is just as possible as in other independent environments. You define your compliance requirements once and can use them everywhere. This is then rounded off with the optional Microsoft AppLocker integration, which also enables context-based application sharing of local applications.
You don’t want to wait, make an appointment with our technical experts!