Features Everything you need for Zero Trust
Context - Individual & Always Up to Date
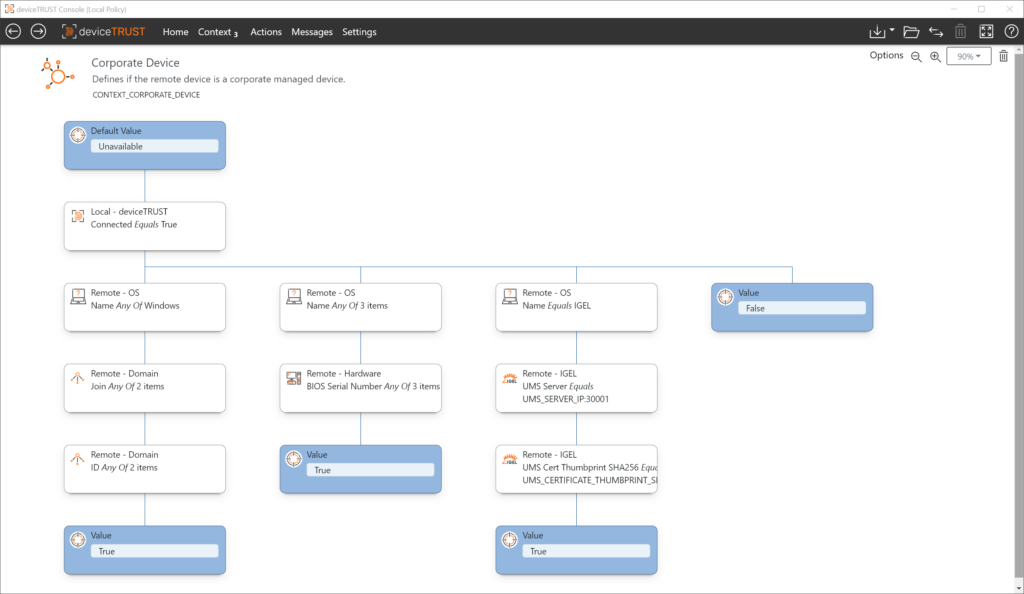
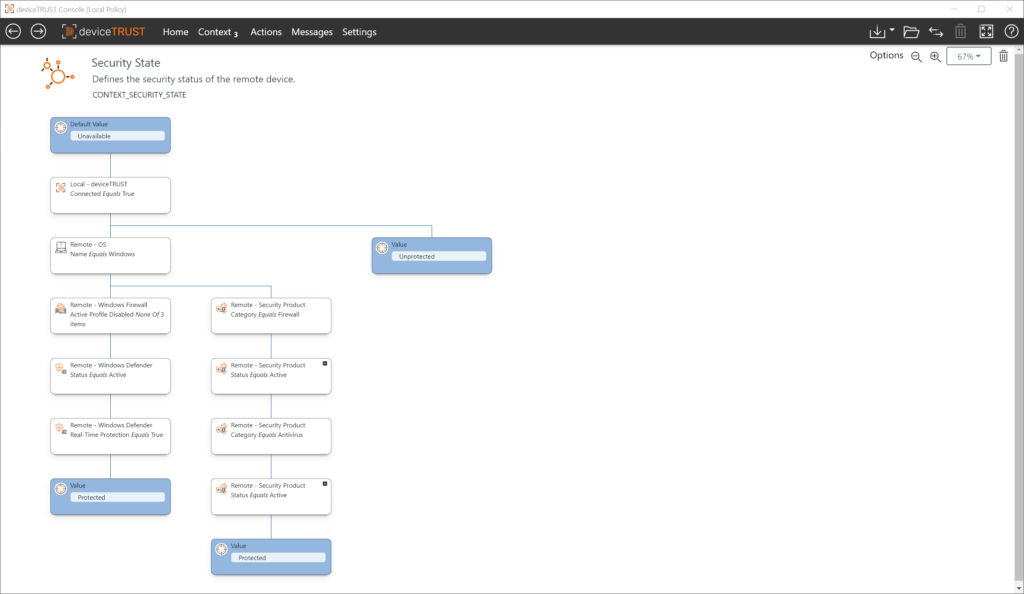
deviceTRUST allows you to define an individual context for your devices. Use the device-related information you need to define an always up-to-date context. Your users’ devices become the next factor!
A granular, always up-to-date context is the basic principle of deviceTRUST’s Contextual Security. We believe that information about your devices should be individually defined and continuously evaluated to support your Zero Trust approach.
Contexts are very individual. Perhaps you only need a single piece of information, or maybe you need to combine multiple properties for your context information. deviceTRUST offers a flexible, easy-to-configure framework to describe your real scenarios and bring them into your configuration.
All properties are evaluated, and all contexts are created continuously. Thus, the information you need to manage your access is always up to date.
Actions - In Real Time
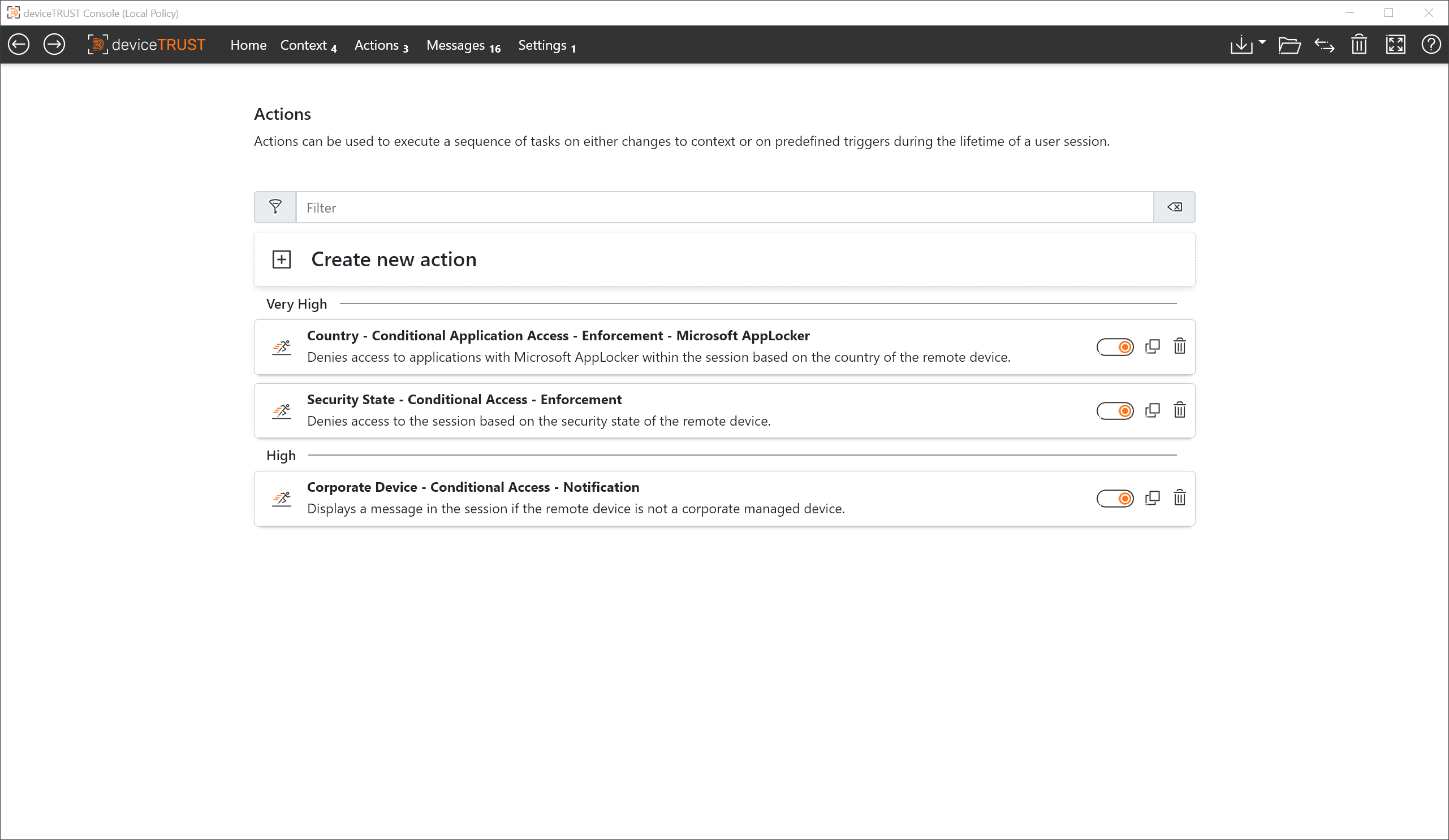
Based on your Context, deviceTRUST runs the Actions you need to protect your environment. Control Access to Workspaces, Sessions, and Applications in Real Time and every situation. Secure access to your data!
deviceTRUST comes with built-in actions that are executed based on your contexts. You can additionally create your own actions and action sequences using APIs.
deviceTRUST’s actions include locking a user’s session, controlling application access, and configuring policies for the user’s digital workspace. Additionally, both OS and 3rd party APIs can be triggered to provide fullest flexibility.
Our direct and always up-to-date approach also applies to actions. Whenever a context change is detected, execution is immediate. Thus, deviceTRUST guarantees immediate security checks in every situation.
Templates - Easily implemented & easy to customize
deviceTRUST’s integrated templates assist with integrating use cases. Based on real-world customer scenarios and years of experience, they are valid for easy, quick implementation and individual customization. Secure your environment in minutes!
deviceTRUST comes with a lightweight console that provides an easy way to integrate your real-world use cases into the configuration. And to support you even better, we have integrated configuration templates to be used as a basis for your scenario. You can either add your data, expand the templates, or combine several of them.
All templates are thoroughly tested and supported. They are based on our experience, as well as on our customers’ scenarios. Would you like to add your own use cases? We are always happy to hear from you!
Building Blocks
Individual contexts and actions that can be used as building blocks within your configuration.
Location Aware Printing
Maps network printers and defines a default printer based on the device placement within a building.
Compliant Application Access
Controls access to applications within the session.
Meeting Room
Controls an idle period for devices based upon whether the device is placed within a meeting room.
Dynamic Policy
Applies a dynamic policy within the session.
Time-based Access
Controls access to the session or applications when accessed outside of working hours.
Geolocation
Validates and controls access based on geolocation information of a device.
Unauthorized USB Device
Denies access to the session when an unauthorized USB device is plugged in.
Building Blocks
Individual contexts and actions that can be used as building blocks within your configuration.
Compliant Backend Access
Display a message or denies access to backend servers when compliance requirements are not satisfied.
License Compliance
Controls access to applications within the session if the remote device is not licensed.
Silo Optimization
Reduces the number of silos by controlling application access for remote devices within a single Silo.
Work From Home
Validates and controls access based on the remote device for home Office users.
BYOD
Controls access to the session or applications when compliance requirements for Bring Your Own Device (BYOD) users are not satisfied.
Dynamic Policy
Applies a dynamic policy within the session.
Location Aware Printing
Maps network printers and defines a default printer based on the device placement within a building.
Status Report
Reports the status of the remote device to various destinations.
Compliance Check
Sets Azure AD properties based on the compliance requirements of a local device.
External Partners
Controls access to the session and applications when compliance requirements for external partners are
not satisfied.
Meeting Room
Controls an idle period for devices based upon whether the device is placed within a meeting room.
Time-based Access
Controls access to the session or applications when accessed outside of working hours.
Compliant Application Access
Controls access to applications within the session.
Geolocation
Validates and controls access based on geolocation information of a device.
Process Monitoring
Controls access to applications or the session based on running processes on the remote device.
Unauthorized USB Device
Denies access to the session when an unauthorized USB device is plugged in.
Compliance Check
Sets Azure AD properties based on the compliance requirements of a local device.
deviceTRUST’s easy-to-implement Contextual Security advances your Zero Trust strategy. By using the device as the next factor, we add further security without increasing complexity, neither for users nor for administrators! The simple Context Framework helps you to collect the properties YOU need and perform the actions to protect YOUR access. In real time, anytime!