In this blog article we show how allowed applications can be controlled very easily – depending on the context of access, device and user. All controls are applied dynamically, not only for login or reconnection, but at any time. Shown are different usage scenarios of our customers, based on different context information.
Introduction Conditional Application Access
For security, compliance, and regulatory reasons, it is often necessary that certain mission-critical applications may only be used under certain conditions.
These conditional application accesses can be configured and administered very easily from a central location using the deviceTRUST Console. In the deviceTRUST Console, our customers can access a variety of different configuration templates for fat client, remoting and DaaS environments for this purpose, which support the implementation of the configuration.
Contextual information, i.e. information about the user, device, network connection and from other sources, can be collected during user login, when unlocking or reconnecting to the digital workplace and during the session runtime. This information can be used to dynamically control access to applications.
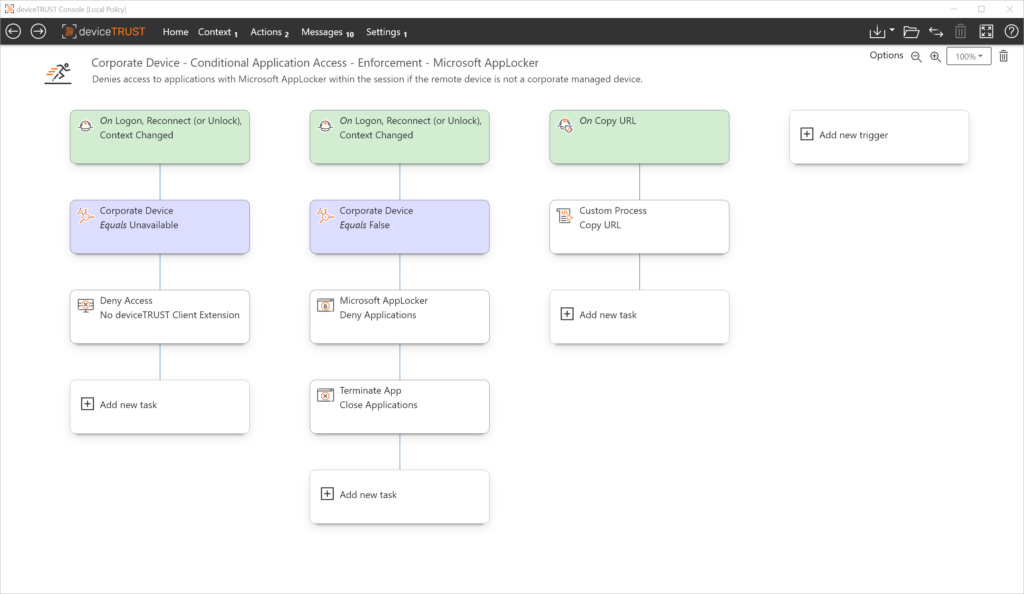
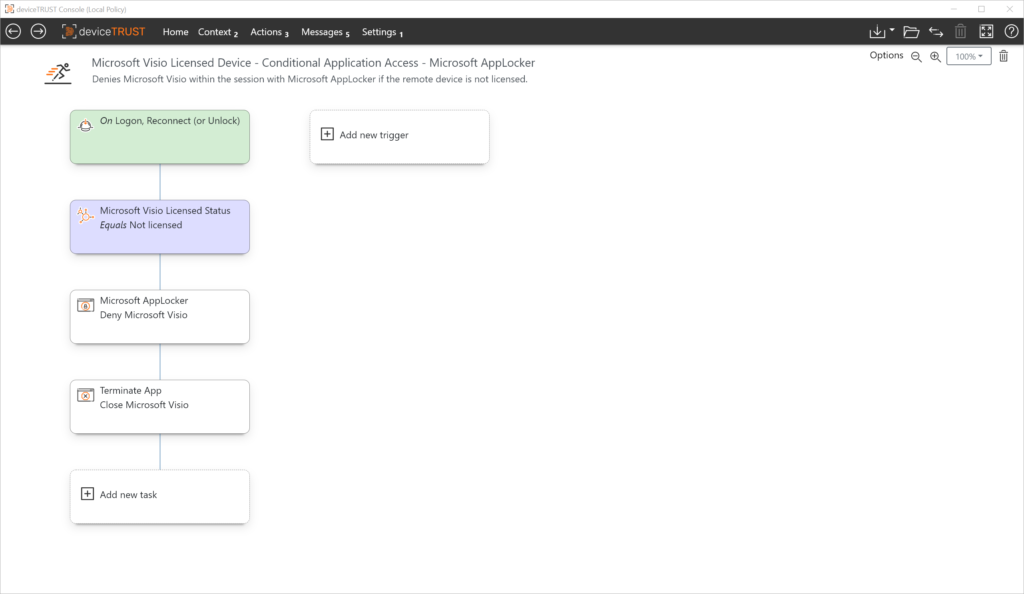
If a context change prevents an application from being used at session runtime, deviceTRUST can safely terminate the instances that are still running. Context as the basis for modern access to digital workstations.
One or more logically linked contexts form the basis for conditional application access control. Depending on the context, dynamic Microsoft AppLocker rules for application access control can be activated by deviceTRUST at any time.
A variety of information is available for context definition that, logically linked together, defines the state of the context. Examples of context information include
Properties of the user object from the Microsoft Active Directory (AD), e.g. the company name or the structure of the email address
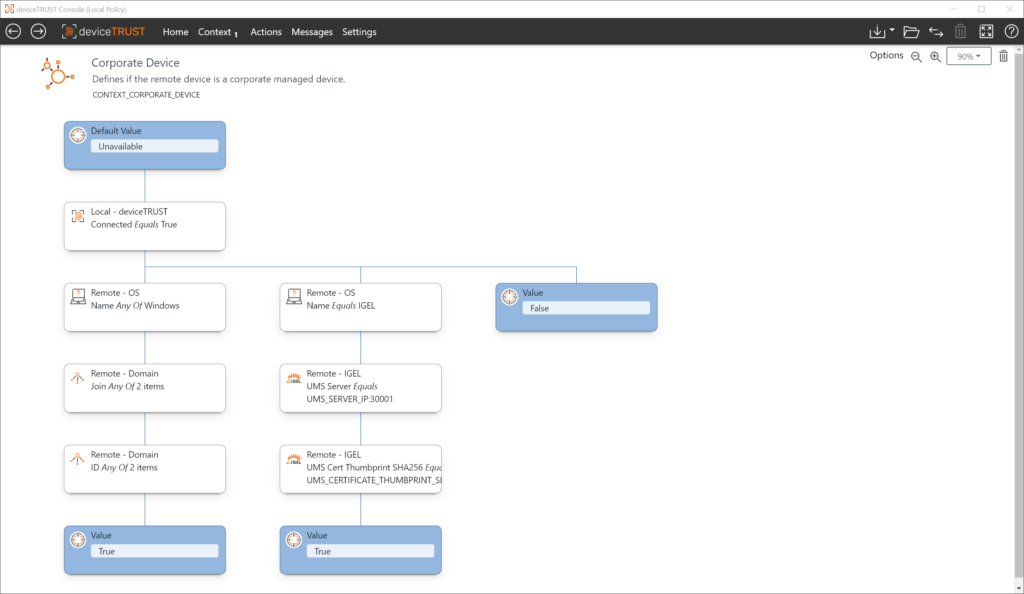
Information about the device in use, e.g., whether it is a company-owned device or the security state
Information about the network used, e.g. the Wi-Fi security status, corporate network, access type or the location of the device
Information e.g. from Microsoft SharePoint lists or text files.
Of course, it depends on the use case which properties and information should be processed. With deviceTRUST our customers are always able to easily define and use very simple or even more complex context requirements.
Application Access Control
For application access control, deviceTRUST can use several methods. APIs of already existing and partly already in the operating system are always used:
- Microsoft AppLocker
- Microsoft FSLogix App Masking
- Microsoft MSIX App Attach
- Microsoft App-V
deviceTRUST extends the role-based function of these solutions with context information and implements rules dynamically.
Examples
These examples show how conditional application access control can be used on fat clients, in remoting or DaaS environments.
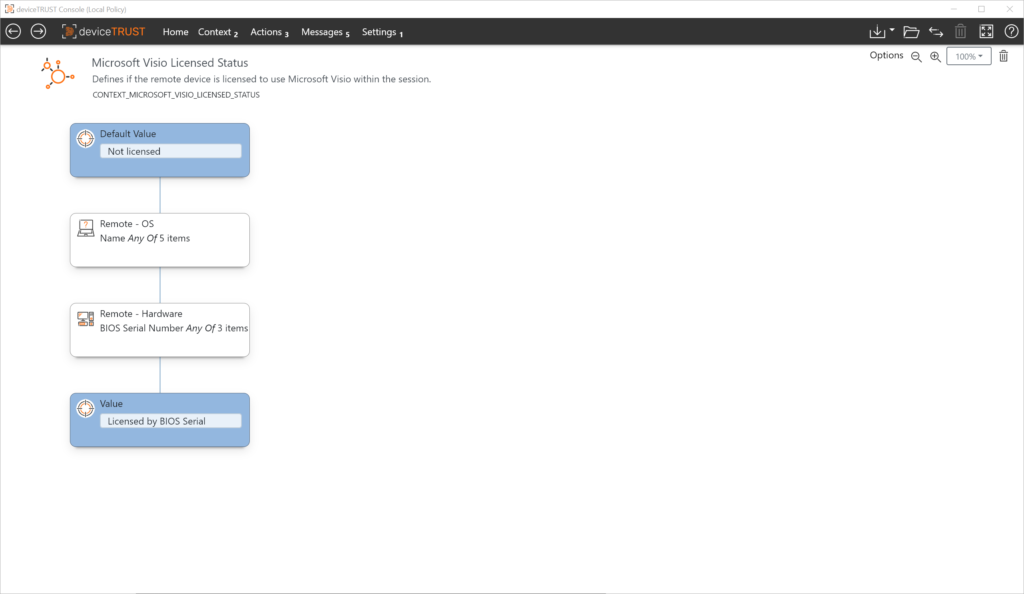
Use Case: Device BIOS Serial Number
In this use case, a particular application should only be usable from specified devices. This can have different reasons, e.g. the license-compliant use of a device-based application within the digital workplace. The devices are identified based on the BIOS serial number, which is unique and cannot be manipulated.
Context
To uniquely identify the device, we use the BIOS serial number in this example. The BIOS serial numbers of all devices that are to be authorized to run appropriately licensed software must be maintained in the list.
Action
Based on the state of the context, application access for unlicensed devices can be controlled when logging in, reconnecting, or unlocking. In addition, running application processes can be terminated if the context changes at session runtime.
Demo
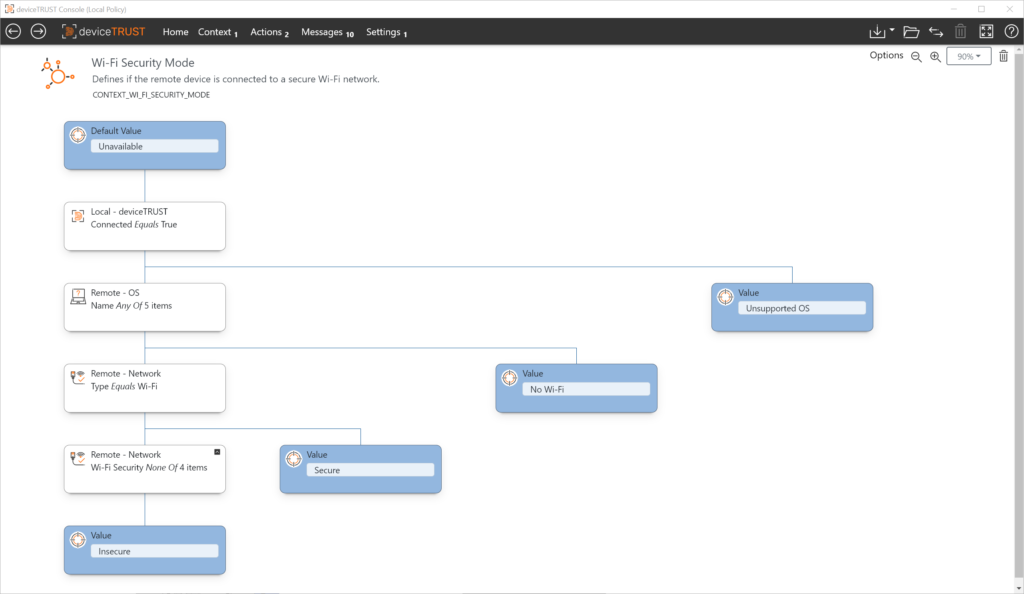
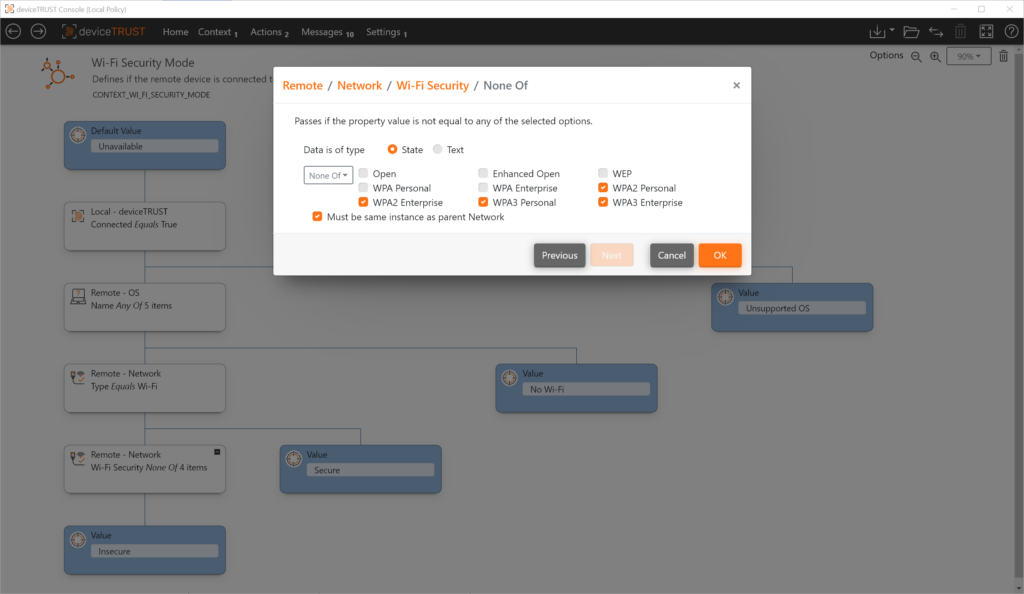
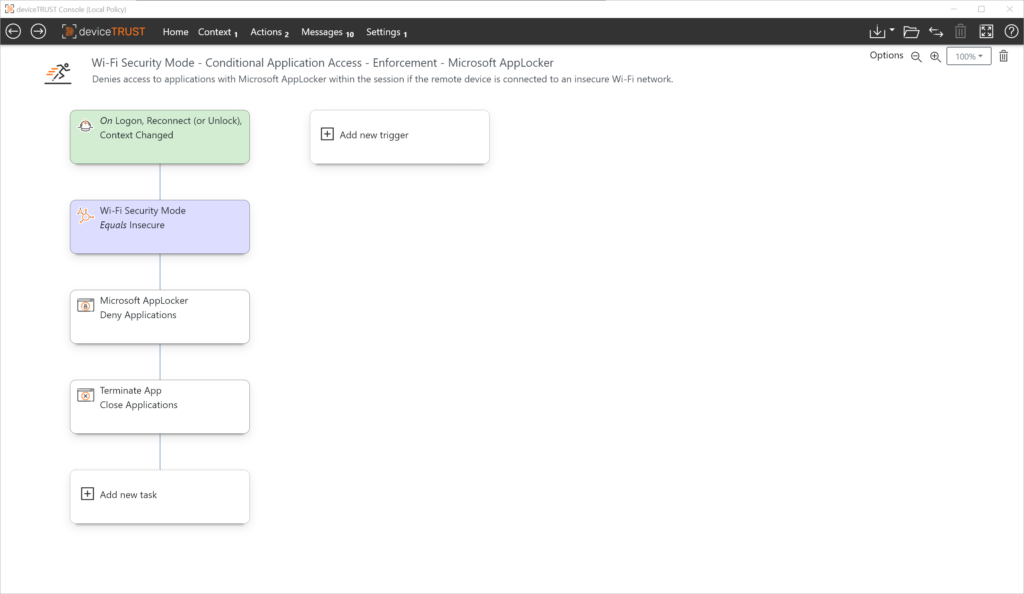
Use Case: Wi-Fi network
In this use case, a particular application should only be usable if the device being used uses a secure network connection. A secure network connection is defined as a connection that uses either no Wi-Fi network or a secure Wi-Fi network (WPA2/WPA3).
Context
Action
Based on the state of the context, application access can be controlled when using insecure Wi-Fi networks during login, reconnect or unblock. In addition, running application processes can be terminated if the context changes at session runtime.
Demo
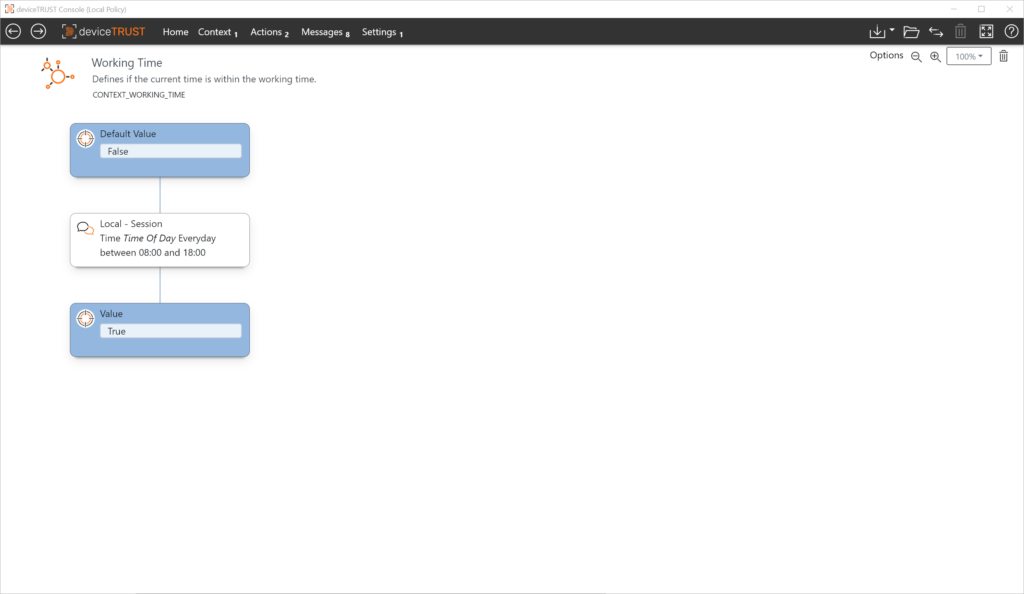
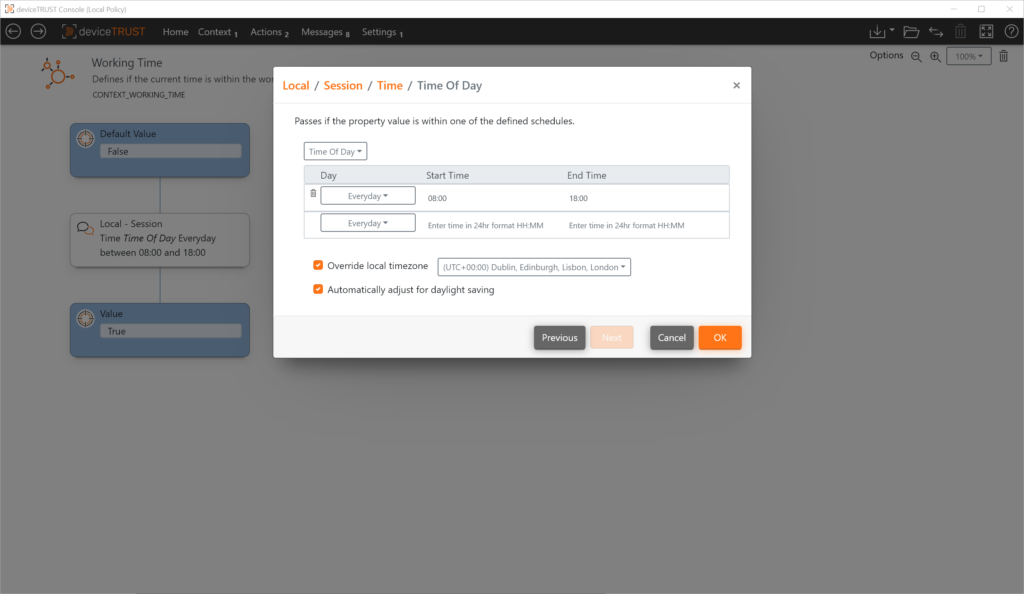
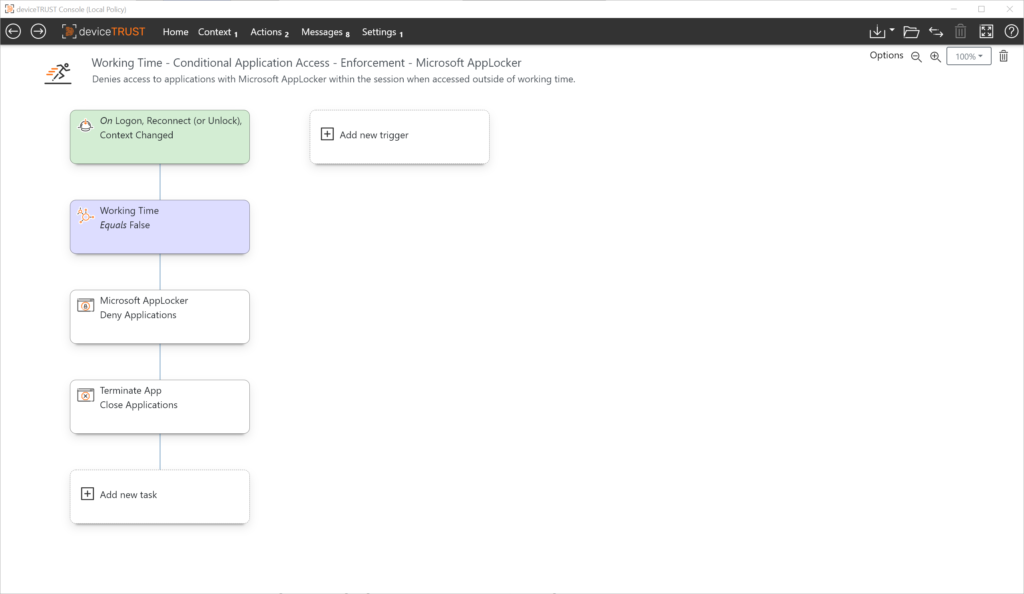
Use Case: Time
In this use case a certain application should only be usable within e.g. working hours. The working time can be flexibly defined for all weekdays including weekends or only for the working week.
Context
Action
Based on the state of the context, application access can be controlled based on the prescribed working time when logging in, reconnecting or unlocking. In addition, running application processes can be terminated if the context changes at session time.
Summary
With deviceTRUST conditional application access can be implemented very easily for fat client, remoting and DaaS environments. Mixed environments, where e.g. fat clients and remoting environments are used together, as well as multi-hop scenarios are supported as well.
If you want to learn more, make an appointment with our technical experts!